Lake Superior State University in Michigan is managing an IT disruption that began around Nov. 10; an internal email described ransomware affecting some campus computers and servers, and Moodle access remained limited as of Sunday.
In a campuswide message reviewed by DysruptionHub, Chief Information Officer Julie Hober said IT is responding to “a ransomware attack that is affecting some campus computers,” has temporarily isolated many systems, and is working with security partners and law enforcement to restore files safely. The message warned users not to engage with related communications.
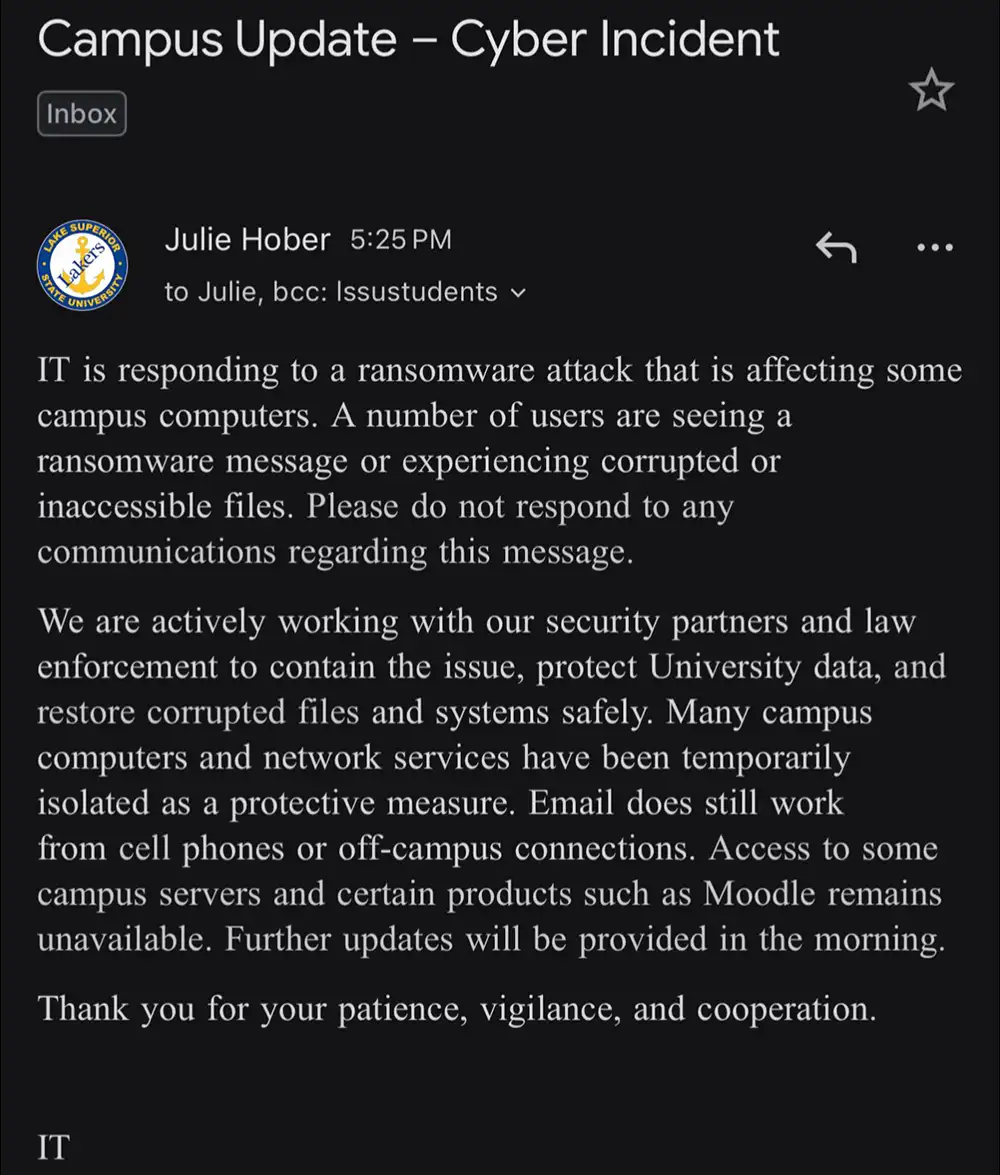
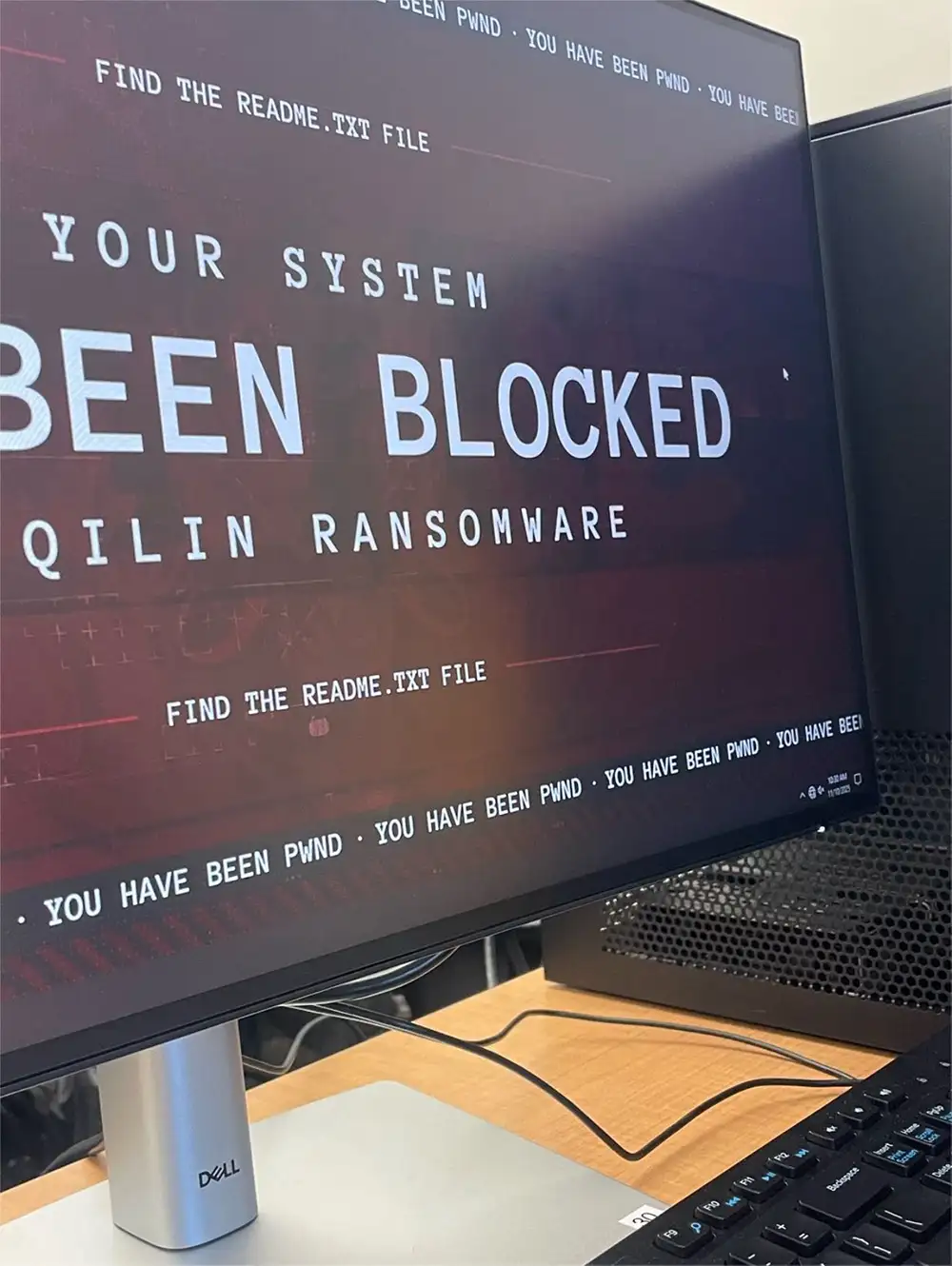
Publicly, the university has not posted a statement labeling the disruption a cyberattack. The website displays a site-wide notice that “We are currently experiencing outages.” Student posts from Nov. 11 showed lab desktops with a lock-screen interface referencing “Qilin ransomware,” and one post called Nov. 11 “day two,” indicating the disruption likely began around Nov. 10. A campus credit-union kiosk also reported its ITM was unavailable that day due to a campus internet outage.
The university has not attributed the incident to any group or reported data theft, and it has not provided a restoration timeline. Class impacts varied by instructor while lab systems were offline, according to student accounts.
Lake Superior State University is a small public university in Sault Ste. Marie with about 1,700 undergraduates. The city saw another high-profile ransomware case earlier this year when the Sault Ste. Marie Tribe of Chippewa Indians suffered an attack that disrupted administration, casinos, and clinics.
Officials said additional updates would follow as recovery continues. The internal email advised the campus community to avoid interacting with suspicious messages and to watch official channels for service restorations.








