Cloud hosting provider CloudCone said a security incident uncovered during an outage first reported Jan. 29 disrupted a limited portion of its Los Angeles hosting infrastructure, and the company’s status page continued to list Los Angeles nodes under a “major incident” as of Feb. 4. The status page labeled the event a “[Major] Hypervisor Outage” and indicated it had been ongoing for about five days.
CloudCone said reinstall tasks were available, but warned reinstalls could take about 3 to 6 hours as the system worked through a queue. Even with reinstalls open, its dashboard continued to show Los Angeles in “major incident” status, while its St. Louis and Reston, Virginia, regions were listed as operational.
![Screenshot of CloudCone’s status page listing VPS Nodes with [US] Los Angeles marked “Major incident” and [US] St. Louis and [US] Reston marked “Operational,” along with Internet Backbone and Networking Gear shown as operational.](https://dysruptionhub.com/content/images/2026/02/cloudcone-status-page-20250204.webp)
The company initially reported service issues on Jan. 29, saying some customers could face network timeouts. Early Jan. 30, CloudCone said monitoring had flagged connectivity problems and abnormal behavior during virtual machine boot on a subset of systems.
CloudCone said it isolated affected servers, identified signs of unauthorized system-level modification on affected virtual machines, and later said evidence pointed to an unauthorized script executed on impacted nodes. The activity appeared to originate through “management-layer access” rather than direct SSH access, CloudCone said, citing a lack of anomalous SSH login records.
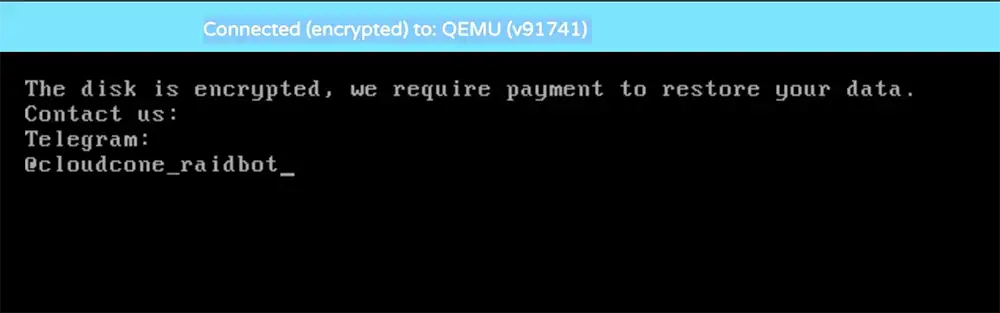
Users also circulated screenshots showing a ransom-style message displayed in online console sessions connected to QEMU, stating the disk was “encrypted” and directing victims to contact a Telegram handle. DysruptionHub could not independently verify whether attackers offered working decryption or recovery in exchange for payment.
Some users and forum commenters described the incident as “encryption,” but CloudCone’s incident narrative and user reports centered on disk-level modification that can render systems unbootable without a typical file-by-file ransomware deployment. Researchers often refer to that pattern as destructive extortion, where attackers pair ransom demands with damage that may not be reversible.
In a statement posted to a hosting forum under the CloudCone name, the company said ransom messages were displayed during boot on affected systems and claimed the boot sectors of impacted VM disks had been overwritten with the ransom note. The post said investigators believed attackers used a Virtualizor management instance and its “Server Terminal” feature to execute commands across connected nodes, after logs tied to that management layer were cleared.
Users circulated screenshots showing a ransom-style message in online console sessions connected to QEMU that claimed the disk was “encrypted,” demanded $100 and directed victims to contact a Telegram handle. Some forum users said they paid but did not receive usable decryption or recovery instructions, though DysruptionHub could not independently verify those claims.
DysruptionHub reviewed on-chain transactions tied to a wallet address circulated in the extortion messages and found the funds were routed through token-swap infrastructure and intermediary wallets before landing at a high-volume “deposit” address consistent with a custodial service. The destination address was not publicly attributed to a specific exchange or threat group.
CloudCone’s incident narrative and user reports emphasized disk-level modification that can render systems unbootable, rather than a typical file-by-file ransomware deployment. Researchers often describe that pattern as destructive extortion, and forum posts suggested the attacker-branded Telegram handle format may have been reused in at least one other VPS incident, raising questions about whether the messaging reflected a single operator, impersonation, or a scam-style tactic.
CloudCone said it found no evidence that customer databases, billing systems, or other internal services were accessed or compromised, and said core systems and billing platforms were unaffected. The company has not publicly quantified how many nodes or customers were affected, whether customer data on virtual disks could be recovered, or whether any customer environments were accessed beyond the affected host infrastructure.
CloudCone did not respond to a request for comment. The company has not publicly described an initial access vector beyond its management-layer explanation, and no group has publicly claimed responsibility.
DysruptionHub could not independently identify external services or organizations disrupted by the outage. CloudCone does not publish a client list and has not publicly disclosed which hosted services were affected, though users on hosting forums reported inaccessible Los Angeles-based servers during the incident.
CloudCone is organized as a Wyoming LLC and lists a mailing address in Sheridan, Wyoming, in company materials and internet registry records. The company also says it maintains operations in Sri Lanka and operates U.S. server locations including Los Angeles, St. Louis and Reston, Virginia, according to its public network listings and announcements.
The incident follows broader warnings from defenders that attackers are increasingly targeting virtualization control planes and management layers. U.S. and Canadian agencies have described PRC-linked use of BRICKSTORM malware in VMware vSphere environments, including vCenter, as a way to maintain long-term access, underscoring how control-plane compromise can create outsized operational disruption even without a confirmed data breach.












