At DysruptionHub we monitor regulatory filings, CTI streams, state breach portals, and takedown advisories for credible cyber incidents affecting U.S. entities. Most tips never make print, either there is no impact or there is not enough to verify. When commercial victims do go public, it is almost always via a required disclosure or a customer notice about stolen data and credit monitoring. That is why a sponsored press-wire blast from a brand-new company saying, essentially, “we were attacked” stopped us cold. In our reporting, we have rarely seen a firm create a news moment around an incident claim without supporting evidence.
PTOE Corporation is a newly formed U.S. venture in the critical-minerals space that promotes a proprietary processing suite it calls System-X. The company says the PTOE name references the Periodic Table of Elements and is pronounced “P-toe.” According to Wyoming filings, the company was incorporated on September 22, 2025, with Northwest Registered Agent Service Inc. listed at 30 N. Gould St., Suite N, Sheridan, Wyoming 82801, as both registered agent and business address (a common mail-drop arrangement that is not evidence of an operating headquarters). The public web footprint is thin. The ptoe.com site shows initial WordPress build activity in late March 2025, a large batch of content posted between late February and early April, and then little visible publishing until an October 14 article about a purported cyberattack. Closely orbiting PTOE is Make America Mineral Independent Again (MAMIA), an aligned initiative that lists overlapping personnel, notably communications lead Lauren Rose, cross-links PTOE as a sponsor, and routes some policy or privacy contact to @ptoe.com addresses, suggesting shared operations rather than arm’s-length separation. Together, PTOE and MAMIA present a politically charged narrative about “mineral independence.” Beyond coordinated press-wire copy and their own sites, there is limited third-party evidence of scale, customers, or technical validation.

So we pulled the thread. What followed looked less like forensics and more like positioning.
The rabbit hole, in brief
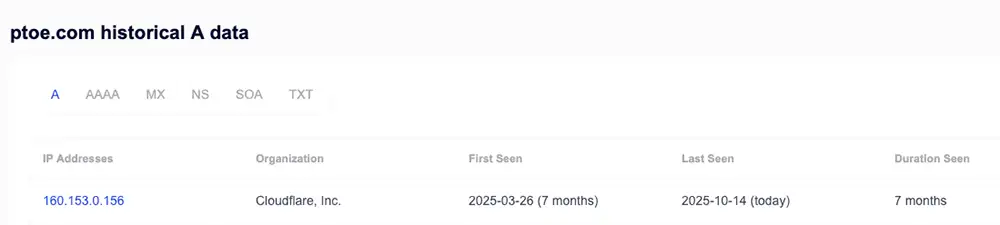
- No DNS hijack signal. Nameservers and the A record for ptoe.com remained stable through the alleged Oct. 7 window. A registrar-level hijack typically leaves an NS swap or an A or CNAME flip. We saw none as of Oct. 15, 2025.
- Site looked normal within a day. Independent scanners hit a healthy WordPress front end, served from GoDaddy with Cloudflare reverse proxy headers and a clean HTTP→HTTPS redirect. No third-party blacklists flagged the homepage at the time of our checks (Oct. 8-15, 2025 UTC).
- Content cadence does not match recovery. The site shows a burst of pages seeded February to April, then months of silence, until a single Oct. 14 blog post narrating the attack and its geopolitics. A DNS incident would not explain a six-month editorial gap.
- Evidence vacuum. The company has not provided a redirect domain, injected code, a vulnerable plugin or CVE, server-log snippets, or registrar change logs. A GoDaddy analyst is identified only as “Allan M,” with no ticket or case number to verify.
- Advocacy halo. A tightly linked initiative, Make America Mineral Independent Again, shares personnel and contact fabric with the company, and trade-press coverage reads like platforming rather than corroboration.
- Dead press inbox. Emails to the listed [email protected] address bounced with “recipient not found.”
- New inconsistency. The release describes both DNS changes and a WordPress plugin exploit; no artifacts for either were provided.
DNS vs. WordPress: you cannot have it both ways without receipts
A DNS hijack occurs at the registrar or nameserver layer and shows up as a visible change, such as an NS swap or an A or CNAME flip. A WordPress redirect compromise occurs on the webserver and leaves DNS untouched. PTOE describes both. Our checks align with the web-application scenario, not DNS.
What a real DNS hijack leaves behind
When domains are hijacked, public things usually move:
- Nameserver changes at the registrar, or registry locks toggled
- A, AAAA, or CNAME flips to attacker-controlled origin
- Certificate-transparency noise, for example new certs for the domain via ACME abuse
- Crawlers and threat feeds capturing the redirect chain or malicious destination
We looked. Those footprints are not there.
What could have happened (most likely scenario)
The evidence points to a routine WordPress compromise, not a DNS hijack. Given the long lull in publishing, the site was likely under-maintained and running an outdated plugin. An opportunistic actor used a known plugin flaw to modify files and add a redirect, either with injected JavaScript or an .htaccess rule, that sent unauthenticated visitors to a Chinese-language storefront. DNS did not change, impact appears limited to the public site, and nothing about the pattern suggests targeting. GoDaddy support likely routed the case to Sucuri (a GoDaddy company) for a standard cleanup that removed injected code, reset credentials, and applied basic hardening. If this is what occurred, there should be straightforward artifacts, such as the redirect URL, server logs showing 30x responses, file diffs, and the plugin name and version.
Why this matters
Words like “DNS attack,” “China,” and “IP theft” carry weight. Using breach-style language without evidence confuses customers, wastes analyst time, and dulls the impact of real alerts. If the incident was a short-lived site redirect, call it that and publish indicators so others can block it. If there was no DNS change and no evidence of targeting, do not frame it as a geopolitical attack. Clear labeling and basic indicators help defenders, while inflated claims erode trust.
Outreach and verification
We attempted to reach PTOE using the press contact listed in its release. Our message to [email protected] bounced with a Microsoft 365 “recipient not found” error, which suggests the mailbox is not set up. No reply was received via that channel as of Oct. 15, 2025 UTC.
What would change our view
We asked for basics and received no reply. We will update if PTOE, or its vendors, can provide any of the following:
- If DNS was altered. A registrar audit showing who, what, and when for NS, A, or CNAME edits on Oct. 7, with ticket or case IDs, plus zone-file diffs before, during, and after
- If WordPress was compromised. The redirect hostname or URLs, a snippet of the injected code (JavaScript, .htaccess, or modified PHP), and the plugin or CVE with patching timeline
- If both occurred. Artifacts for both layers, plus third-party confirmation from GoDaddy or Sucuri, including a named contact and a case reference
Until then, the most responsible characterization is that there is no corroborated DNS hijack and no substantiated attack beyond a claim.
The story that does not track
In the real world, verified breaches surface through regulatory filings, customer notices, or technical advisories with artifacts, such as IOCs, ticket numbers, and diffs. Here, a brand-new company with minimal footprint used a paid press wire to announce an attack without evidence, and the listed media contact’s mailbox does not exist. That is not how incident response or crisis communications works. That is how you generate publicity without substantiating details.
The pattern we found is internally consistent, but not with a breach:
- New shell-style footprint, registered-agent address and little public substance
- Site seeded in bulk, then months of silence, not a restoration cadence
- No external signals of DNS tampering during the claimed window
- Advocacy framing tying a routine WordPress setup to great-power intrigue
- Press address bounces, no third-party confirmations, a first-name-only “Allan”
- Layer mixing in the press release, simultaneous DNS and plugin claims, with no supporting artifacts for either
If something happened at all, Occam’s razor says garden-variety WordPress redirect malware, short-lived, no DNS change, easily cleaned. But the company did not provide a redirect domain, plugin or CVE, logs, or case numbers. Instead, it offered a geopolitical narrative and a broken media contact.
What this was likely about
We cannot know motive, but three plausible explanations fit the evidence better than a DNS hijack:
- Legitimacy by PR. Use a “we were attacked” hook to seed brand mentions and backlinks around “System-X” and mineral politics.
- Advocacy halo. Cross-promote the Make America Mineral Independent Again initiative by casting PTOE as a targeted actor.
- Comms misfire. An overzealous spokesperson packaged a minor web hiccup as a state-linked campaign, then failed basic comms hygiene.
None of those require a DNS event, and none justify a press-wire breach announcement without receipts.
Our stance
We are open to updating this analysis if PTOE provides verifiable artifacts or third-party confirmations, and we will correct the record promptly if new evidence warrants it.
Company response (received Oct. 17, 2025, 10:59 a.m. ET)
- Timeline: PTOE says the issue was first detected on Oct. 7 at approximately 14:20 (timezone not specified). Service was fully restored by Oct. 9 at 01:30 after a site sweep, malware removal, and “DNS verification” by GoDaddy.
- Nature of the incident: PTOE states a WordPress plugin vulnerability was exploited to inject a redirect script that sent visitors to a Chinese-language shopping portal with malware links.
- Third parties: PTOE provided a written line it attributes to ‘Allan M,’ described as a GoDaddy Senior Security Analyst, stating the site was cleaned and secured.
- Remediation: PTOE says the vulnerable component was removed and that they implemented 24/7 firewall and malware monitoring through Sucuri, MFA on admin access, and automated integrity audits every 12 hours.
- Attribution: PTOE says it cannot state definitively that the incident was state-sponsored but believes the timing and “code signatures” suggest PRC-linked actors.
We have Lauren Rose’s email on file.
Our note on verification
We have not received artifacts that would allow independent verification of PTOE’s claims, such as the plugin name and version, the redirect hostname or URLs, samples of injected code, server-log excerpts showing redirects, Google Search Console notices, or case/ticket numbers from GoDaddy or Sucuri. We did not observe Sucuri WAF indicators in DNS or headers during our checks; that does not preclude Sucuri providing cleanup or monitoring. PTOE’s reference to “DNS verification by GoDaddy” is consistent with our finding that public DNS records did not change during the window.








